FL01-1: Intro to Cyber-Aerial Computing
In this module, you will be introduced to aerial computing as novel paradigm combining aerial radio access networks and edge computing to address the limitations of existing systems and a research gap in comprehensive computing architectures. This new architecture features low-altitude, high-altitude, and satellite computing platforms, offering attributes like global service, enhanced mobility, higher scalability, availability, and simultaneity. We will discuss key enabling technologies such as energy refilling, network softwarization, frequency spectrum, multiaccess techniques, AI, and big data, alongside its applications in vertical domains like smart cities, smart vehicles, smart factories, and smart grids, while also outlining associated challenges

FL01-2: Assembling Crazyflie Drone
In this module, you will begin by learning how to unpack, assemble, and test the Crazyflie 2.1+ drone. It is essential that you carefully review the provided materials before attending the lab sessions, as this preparation will enable you to program and test the drone more effectively during hands-on activities. Remember, your lab will be completed in pairs. If you do not pay close attention to this online self-study, you may be unprepared and unable to contribute effectively during the lab session.

FL07-1: Drone Delivery and Your Privacy
In this module, you will learn about the emerging privacy risks associated with drone package delivery systems, specifically when drones are required to broadcast their position, allowing third-party observers to link customers to vendors and their purchases. The authors propose a probabilistic definition of privacy risk based on the likelihood of correctly associating a customer with a vendor given a delivery route. The work then explores various strategies to mitigate these risks, such as aggregating multiple orders and incorporating "decoy vendors" into delivery routes, while also analyzing the trade-offs between privacy and delivery efficiency (wait times). Finally, the paper introduces and evaluates routing heuristics designed to generate routes with built-in privacy guarantees, examining how different geographical distributions impact the balance between privacy protection and operational efficiency.

FL09: Post-Disaster Recovery (Cont.)
In this module, you will continue learning about the framework designed to accelerate drone-centric search operations during post-disaster relief, particularly for non-professional pilots like rescue crews. The framework, known as FastPlan, integrates three key components—map extraction, clustering, and path planning—to automate and simplify complex drone missions. Through this lesson, you will explore how density- and distance-aware algorithms enable drones to efficiently identify, group, and navigate among points of interest (POIs) in disaster-affected areas. You will also analyze how the density-aware path planning technique supports decision-making in time-sensitive operations, such as determining which scan point should be visited first, how to balance energy use and search coverage, and how different path strategies (e.g., Density First, Nearest Neighbor First, Density and Distance, and Random) affect mission performance. Finally, this module will connect theory to practice by demonstrating the use of the FastPlan mobile application, which automates these processes to reduce manual setup time, allowing rescue teams with minimal drone expertise to quickly deploy aerial searches, locate survivors, and adapt to rapidly changing environments.

FL05: Project #2 SkyGame
In this module, you will read through Project #2 SkyGame description. It is essential that you carefully review the provided materials before attending the lab sessions, as this preparation will enable you to program and test the drone more effectively during hands-on activities.

FL00: Policing with Drones
In this module, you will engage in self-study to explore how drones are used in policing. Your activities will include analyzing a news article, examining a policy research study, and completing an interactive video with embedded quizzes to reinforce the key concepts.

FL02-1: Drone Operation Federal Laws and Regulations
In this module, you will explore real-world cases that highlight the application of U.S. laws and regulations governing drone operations. These cases illustrate how improper or unlawful drone use can lead to serious consequences, including legal action, threats to public safety, and ethical dilemmas. By reviewing these examples, you will gain a deeper understanding of how regulations are enforced, why they are necessary, and how they intersect with broader issues of privacy, security, and responsible technology use. Also, you will review the lecture notes from Dr. Sunho Lim. Be sure to review the lecture notes before watching the video, as they will help you answer the embedded questions more effectively.

FL 10: Privacy Protection
In this module, you will learn about an innovative sky caching–aided spatial querying framework that employs drones to enhance users’ location privacy in location-based services (LBS). To mitigate privacy risks from sharing location data with untrusted LBS servers, the approach enables users and their drones to collaboratively generate dummy locations to achieve k-anonymity. The authors introduce and assess three cache admission control (CAC) strategies—switched, filtered, and forward—to efficiently manage cached query results and minimize redundancy between user and drone. Simulation results using OMNeT++ show that the proposed drone-assisted method significantly reduces the number of queries sent to the server and enlarges the cloaking area, thereby enhancing overall location privacy. This research redefines the role of drones, positioning them not as privacy threats but as privacy-preserving agents in spatial querying systems.

FL06: User Location Privacy
In this module, you will learn about the critical problem of user location privacy in modern mobile apps and the broader, largely unregulated location-tracking industry. You will begin with the limits of binary consent (opt-in/deny) in location-based services (LBS) and study finer-grained controls—including GPS perturbation that can intentionally “lie” within default privacy zones so that local search results remain accurate while exact coordinates are obscured. You will then learn about how to situate these designs in real-world risk: a commercial ecosystem in which dozens of firms continuously log movements from mobile apps, compile massive datasets, and enable de-anonymization that can reconstruct intimate “life diaries” (e.g., home, health visits, political activity), undermining claims of consent, anonymity, and security. You will be able to explain LBS privacy risks, prototype privacy-preserving controls, evaluate re-identification risk, and articulate why personal control and informed decision-making must be paired with policy and governance to curb a de facto, privately run surveillance system.

FL04-1: Privacy Preserving Target Tracking
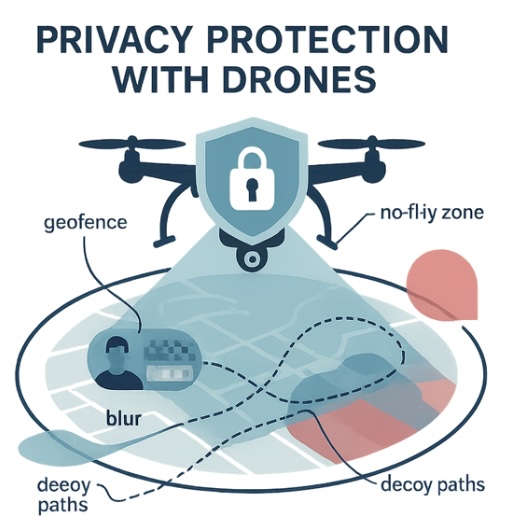
In this module, you will learn about privacy preserving target tracking, strategies for protecting the location and trajectory privacy of drones while they are engaged in tracking a target. Privacy-preserving target tracking is a drone-tracking approach that flips the usual privacy focus (protecting people from drones) to instead protect the drone’s own location and trajectory from adversaries while it pursues a target. Rather than flying a predictable shortest path that reveals where the drone is and where it is headed, the tracker obfuscates its position and randomizes its route—for example, by inserting randomized or dummy intermediate waypoints and bundling its true location with decoys when querying a server—so an eavesdropper or colluding target cannot reliably infer or forecast its movement. Engage in this module to learn more about privacy preserving target tracking.
FL04-2: Project #1 SkyPRWP Part 2
In this module, you will read through Project #1 Part 2: SkyPRWP’s description. It is essential that you carefully review the provided materials before attending the lab sessions, as this preparation will enable you to program and test the drone more effectively during hands-on activities.

FL02-2: Project #0 HelloDrone
In this module, you will begin by learning how to install and setup a drone programming environment. It is essential that you carefully review the provided materials before attending the lab sessions, as this preparation will enable you to program and test the drone more effectively during hands-on activities. Remember, your lab will be completed in pairs. If you do not pay close attention to this online self-study, you may be unprepared and unable to contribute effectively during the lab session.

FL03-2: Project #1 SkyPRWP Part 1
In this module, you will read through Project #1 SkyPRWP Part 1’s description. It is essential that you carefully review the provided materials before attending the lab sessions, as this preparation will enable you to program and test the drone more effectively during hands-on activities.

FL07-2: Project 3 SkySenor – Part 1: Hand-Guided Flight
In this module, you will read through Project #3 SkySensor – Part 1: Hand-Guided Flight description. It is essential that you carefully review the provided materials before attending the lab sessions, as this preparation will enable you to program and test the drone more effectively during hands-on activities.